Ransomware attacks stay steady – yet with a couple of basic advances, associations can avoid succumbing.
Individual Cybersecurity mindfulness turned into a need in the current circumstance of expanding computerized change. Either at the business level or people, you want to safeguard your character, records, cash, etc.
The quantity of ransomware attacks has dramatically increased in the course of the last year as cyber criminals proceed with their constant missions to hold organizations and information to emancipate.
As indicated by an examination by cybersecurity analysts at SonicWall, the volume of endeavored ransomware attacks focusing on their clients rose by 105% in 2021, to an aggregate of 623.3 million endeavored episodes consistently.
The figure additionally addresses more than triple the quantity of endeavored ransomware attacks recorded in 2019.
The greatest flood in ransomware attacks divided June and September 2021, a period that included the absolute most critical episodes of the year before.
These incorporated the Colonial Pipeline ransomware assault, the JBS ransomware assault, and the Kaseya ransomware assault.
Both Colonial and JBS were among the ransomware casualties that picked to pay cyber criminals a huge number of dollars in deliver requests to get a decryption key to reestablish their organizations.
Cybersecurity suppliers and law enforcement agencies advise against yielding to emancipate requests, as it shows criminals that ransomware attacks work. However, sometimes, casualties see it to be the most productive approach to reestablishing the organization, albeit even with the right decryption key, this can in any case require a very long time of exertion.
Cyber criminals are likewise utilizing the additional influence gave by taking steps to spill information taken from compromised networks on the off chance that they don’t get a payment installment.
As indicated by SonicWall’s insights, the United States was by a wide margin the biggest objective for ransomware attacks, yet the volume of recognized episodes dramatically increased in numerous districts all over the planet including Europe and Asia.
While move has been made against some huge ransomware gatherings, for example, the evident takedown of REvil in January, the SonicWall report cautions that this has been “largely ineffective” in stemming the tide of ransomware overall.
Because of the lucrative nature of ransomware, when one gathering is brought down, new ones ascend to make up for the shortcoming.
says the paper
Yet, in spite of the proceeding with scourge of ransomware, as indicated by SolarWinds, there are somewhat basic advances that associations can take to keep them from succumbing, for example, rehearsing better secret key cleanliness and utilizing multifaceted verification.
Check the Email Address and Domain Name (Link)
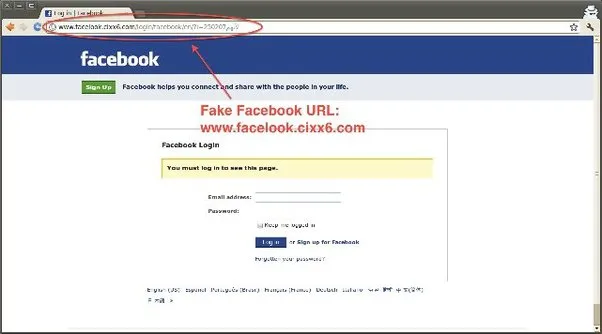
At the point when you get an email or open a URL, you should ensure the domain name and the source’s email address. For instance, you might open some URL that shows up as an authentic-looking Facebook site.
Yet, assuming that you check the domain name above in the domain box, you might observe something like “facebook.example.com“. This isn’t the Facebook unique domain name, or you might find something other than what’s expected, for example, faceboök.com; notice here is an alternate (o) letter. A similar applies to the email address.
These phony domains/email address intends to beguile and phishing you. With the phony Facebook URL, assuming you sign in entering your username and secret phrase, the programmer on the opposite side will take them and will hack your Facebook account.
What is Web 3.0 and why is it significant?
In the phony email case, they maybe attempt to persuade you to pay some cash or give them some basic data guaranteeing that they are from the Google security group or Paypal, and so forth Along these lines, cautiously browse the email source address.
Automatic Security Updates
For your gadgets’ software, from the working framework (Windows, Android, Mac, and so forth) to the program expansion, you should set each application and software on your gadgets to the auto-update choice.
Refreshing software adds new highlights and empowers software organizations to fix bugs and eliminate basic weaknesses that programmers exploit to make their attacks.
Notwithstanding the awfulness created by the expansion of cyber dangers, by refreshing all your softwares, you have almost halfway towards appreciating secure registering and web perusing.
What’s more, you want to refresh consistently your Antivirus and Firewall applications.
This was notable for quite a while on the PCs, yet it’s recently become likewise suggested for cell phones, however telephones actually don’t make introducing Antivirus obligatory as in Windows OS.
The advantages of refreshing security software are to keep them with the most recent patterns of cyberattacks. This safeguards your gadgets from new malignant records and infections successfully and protects your information from attacks that harm or take them.
Avoid Following and Clicking Unknown Links
Clicking anyplace without examining the site’s authenticity or downloading a connection without knowing the email source might cause entering pernicious software into your gadget.
It could be a contaminated URL that causes introducing ransomware that locks your admittance to your information except if you pay cash for the programmer.
Likewise, it’s prescribed to introduce some program modules that block programmed downloading of any contents or Java, though streak module content can have malevolent code.
As to, you shouldn’t unveil your secret phrase and delicate data to anybody.
Additionally, when you use multifaceted validation that consolidates different sorts of certifications, face, finger impression, SMS based confirmation to your telephone with a one-use code, don’t give this SMS code to any individual.
For instance, a few assailants request that you give them this code to go along with you for a Whatsapp bunch, don’t give them.
As a general rule, specialists said sharing isn’t mindful, for your accreditations as well as in any event, for quite a bit of your own data. It’s prescribed to share the base measure of individual data on social media.
Additionally, Check your protection settings on every one of your social media accounts, particularly on Facebook.
Avoid Easy Passwords
Secret word ought to be not difficult to recollect, however this makes it simple to find!
Assailants use word reference based software to attempt from a large number of possibles and the most normally utilized passwords.
Kindly avoid explicitly those best 200 simple passwords simple to find. Plus, don’t utilize your name, family name, birthday, or individual thing as a secret phrase; programmers can make surprising examinations about your life.
Breaking straightforward passwords is probably the least demanding way for cyber criminals to get to records and organizations, especially assuming that they’re normal passwords, or the username and secret key have recently been spilled in a break. Utilizing novel passwords on records can assist with forestalling unapproved access.
How to cause a secret key that to is not difficult to recollect for yourself and difficult to find for programmers? You should made a mind boggling secret word, however such that you can recollect it.
Web App Development & Advantages – Everything You Need to Know.
For instance, take the main letters of certain statements; this makes them a new nondictionary word. Then, at that point, adjust it for certain numbers and images to expand its power.
The secret key additionally should be a long one.
Furthermore it might be ideal on the off chance that you involved an alternate secret word for each unique login, so you want Password Manager software. It makes you really want just to recollect one long secret word for all your logins, and it’s known as the Master Password.
Be Aware of Social Engineering (Hacking and Deception)
Social Engineering is utilized commonly in promoting and legislative issues.
In any case, in the cyberworld, it’s utilized now and then for hacking and trickiness. By acquiring your certainty to give them a portion of your certifications, they stunt you into penetrating your information. It’s become more straightforward with the cell phone.
Social Engineering beguiling did not depend on innovation weaknesses yet human or client conduct. Beguiling by Social Engineering existed before PCs, yet PCs and cell phones make it simpler to do. In any case, we ought not fear utilizing advanced innovation assuming that we genuinely get it.
To avoid Social Engineering, know about a few secret self-predispositions. For instance, you have an email guarantee that you should answer direly in 24 hours to get your legacy and that you should give them your secret phrase or send them some cash or your secret phrase.
Another model, when they are taking advantage of regard for an authority, for example, police or your supervisor to give them your secret key. In everything cases, don’t give the secret phrase to anybody.
Likewise, applying multifaceted validation across the organization gives an additional a hindrance of insurance against programmers endeavoring to penetrate a record.



