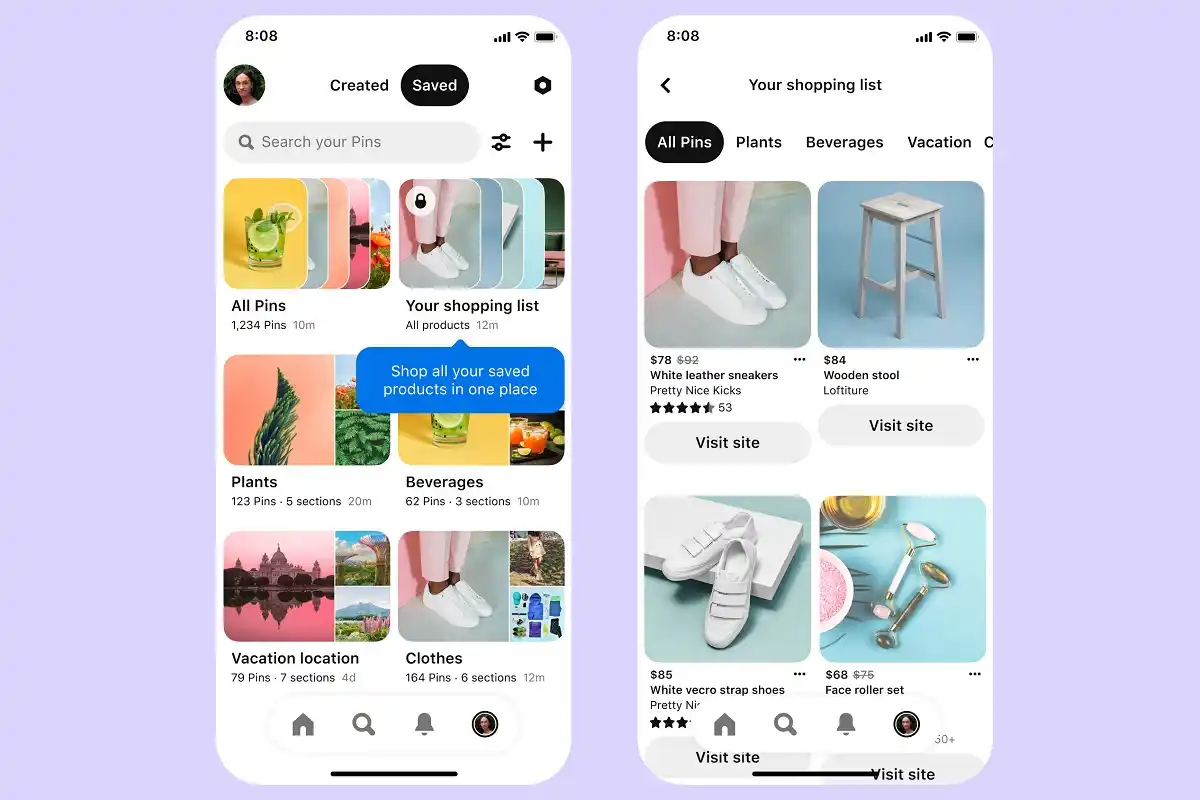
E-Commerce sites will generally be a hot target for cyberattacks. For would-be thieves, they are treasure troves of personal and financial data. And for businesses of all sizes, the expense of a breach both in loss of data and customer trust can be hugely damaging for businesses of all sizes.
E-Commerce business owners are too aware of these issues and are increasing their security measures. The VMWare Carbon Black 2020 Cybersecurity Outlook Report viewed that 77% of businesses surveyed had purchased new security products somewhat recently and 69% had increased security staff.
In this constant game of cat and mouse, as online retailers add increasingly innovative technologies to their sites to remain competitive, cyber attackers are equally improving their abilities and tracking down new vulnerabilities to exploit. The best method for remaining ahead is to be aware of eCommerce security best practices and the types of attacks to be keeping watch for.
Best Practices for eCommerce Security
The compliance standards mentioned above aren’t disappearing. Truth be told, trends in privacy concerns indicate that we ought to expect more regulations in the future as people of all ages are increasingly concerned with where their data is going.
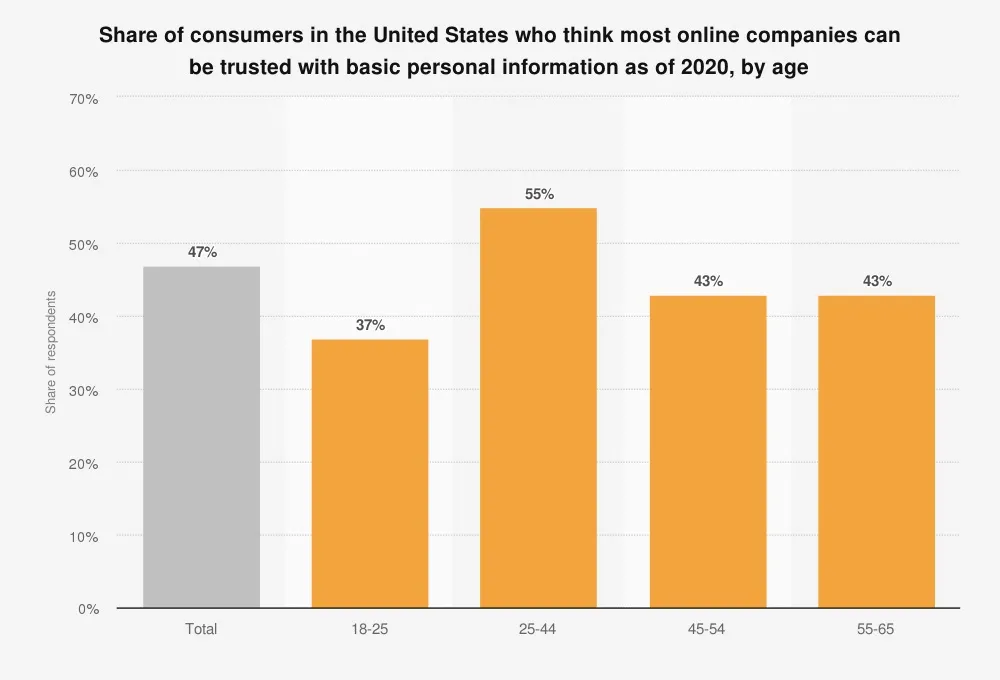
This Data Breach Investigations Report dives deeper into trends in retail cyber attacks. Payment information is demonstrated to be the prominent target, and eCommerce attacks continue to rise as point-of-sale breaches and card skimmers are, overall, declining.
Assuming a security breach of your eCommerce site leads to a deficiency of customer data, the associated fines, and a hit to your brand reputation could be devastating.
Solid, Unique Passwords
As indicated by the 2020 Verizon Data Breach Investigations Report, 37% of credential theft breaches used stolen or weak credentials. It merits the extra effort to make sure you, your employees, and your customers implement great practices areas of strength for:
- Solid passwords are something like eight characters and contain upper and lowercase letters, numbers, and symbols.
- Passwords ought to never be shared, each user ought to have their own unique, private username and secret phrase for login.
- Never use the same secret key for other login credentials as you use for your eCommerce site.
- Consider utilizing a secret key manager.
- Never freely share sensitive information like your date of birth, social security number, or some other data you might use as answers to security questions.
Use no type of the default admin name provided. Attackers write scripts that run constantly attempting over and over to sign in to the admin panel, assuming you’ve used anything like “admin”, they are more likely to break it.
Device Protection
Whether you have one computer in a home office or a headquarters with a full networked computer system, make sure your connected devices are cyber secure with anti-virus software, firewalls, or another appropriate method of protecting against threats.
Beware of Social Engineering Attempts
One of the best ways of keeping away from malware infections is to abstain from falling into phishing traps. Never provide any level of personal information unless you have verified the identity of the recipient.
Furthermore, no legitimate association will ever request that you share your secret word.
Never click join in dubious emails, as they might take you to a webpage that is made to seem to be a natural login page yet serves instead to steal your information. And download no attachments that you were not already expecting.
There are a few methods for recognizing phishing attempts from legitimate emails; here’s what to search for:
- Clear spelling and syntactic mistakes in the subject line or body of an email could indicate a dubious sender.
- Check out closely at the area of the email sender. They are often made to appear as though a recognizable space yet are off by only one letter.
- The same goes for any URLs you could click. From the outset, they might appear legitimate, yet the spelling could be off by one letter in the hopes you don’t notice and snap-in any case to a dangerous space.
- Dubious emails might request that you follow through with something like transfer money or authorize a charge and offer an excuse for why it should be done immediately.
Additional Authentication Factors
It might feel like a burden on occasion, yet utilizing 2-step verification, 2-factor authentication, or multifaceted authentication gives you further assurance that you and your authorized users are the main people signing into your store.
Considering the potential consequences of a breach, it’s worth the effort.
Customer Data
When it comes to storing data, the bottom line is to never clutch more than you need to ideally lead your business. However, in deciding how exactly that affects you, there are a ton of factors to consider.
Especially with the developing number of data privacy regulations, it’s vital to carefully establish your own business theory to balance customer experience, business convenience, and security.
Continuously keep your customers’ basic data separate from other information by segmenting your network. Deploy firewalls and direct reviews to ensure that all of your security measures are working how they are supposed to.
Up-To-Date Website
Security is a persistent cat-and-mouse game. Attackers identify vulnerabilities; software engineers fix them.
Assuming that you are utilizing a SaaS eCommerce stage, updates to your software are taken care of automatically. In any case, with on-premises eCommerce arrangements, your business is responsible for implementing any updates, bug fixes, or vulnerability patches to the software that powers your store.
Data Back-Up
Assuming that you are breached and lose access to your data, you will believe a reinforcement should help you get your business back ready as fast as could be expected.
Plugins and 3rd Part Integrations
Take an inventory of all the outsider arrangements you’re running inside your store. Make sure that you know what they are and assess your continued level of trust in that outsider.
Assuming you’re done utilizing them, remove that integration from your store. The idea is to permit the fewest number of parties to have access to your customer’s data, while as yet driving your business forward.
HTTPS
Secure HTTPS facilitating, which requires an SSL certificate, will help secure your website.
It’s likewise an aid for your marketing department because Google penalizes websites with HTTP in natural search rankings. HTTPS sends a positive trust sign to your shoppers, especially the carefully sharp ones.
Security During the Holiday Season
The Christmas season is, unfortunately, a time you can expect higher volumes of attempted misrepresentation and cybercrime.
Everyone is really occupied, and there are huge spikes in rush hour gridlock on eCommerce sites, making abnormal behavior more challenging to protect. Attackers know this and see it as an open door.
Here are some things you can do to ensure website security through special times of the year:
Pre-Holiday Security Check
The Christmas season is the time when a decent greater part of eCommerce cyber-attacks take place, exploiting the occasion rush. Retailers ought to prepare for this in advance and lead an intensive security check before the Christmas season begins.
This ought to include checking for malware in point-of-sale systems and working on the security of web servers.
Your vacation security review ought to likewise include an examination of who approaches what:
Make sure to review admin-level records and privileges for your store, marketing software, and other tools. Disable or delete unused records. Update permissions to reflect the genuine work processes for specific users.
Fraud protection
A steep spike in shoppers is often accompanied by an increase in fraudulent movement. As indicated by the Retail Fraud Survey from 2019, 46% of customers are concerned about being the casualty of misrepresentation when shopping this Christmas season.
Another type of cyber hazard and one of the biggest dangers to eCommerce brands today is the chargeback trick. Attackers acquire credit card information alongside credentials and go on a spending spree.
The retailer gets an order and ships it not mulling over it. Just to receive a chargeback at some point in the future because the charge was marked as extortion. The retailer can’t argue and is forced to refund the order and the merchandise is a distant memory. This is even compounded more with reliability projects and gift vouchers.
This type of cyber misrepresentation is very difficult to prevent. After losing 1000s in the merchandise.
Support Team and Security Update
Make sure you and your team are prepared for normal threats, including having a clear process for verifying the identity of customers who request any changes to their orders or records.
It’s a word of wisdom to get your store pretty much locked down for these special seasons and not make too many changes to it, just to keep away from the extra gamble that that can entail. Yet, that general guideline does not matter when it comes to security and fixing your site for any vulnerabilities.
This is generally applicable assuming you have an on-premise eCommerce arrangement. You need to have a tried and true arrangement for site updates on the off chance that they become necessary to ensure the security of your business and your shoppers.